20+ wireshark network diagram
But I could not find it. Navigate to Statistics Flow Graph select TCP flow and click OK.
Can Wireshark Capture All Network Traffic Quora
Whereas a web proxy such as Fiddler is focused on HTTPHTTPS traffic Wireshark allows deep packet inspection of multiple protocols at multiple layers.
. USBtin is mapped to serial port devACMx Linux MacOS or COMx Windows. Engineering Computer Science QA Library Explain the term structured exception handling SEH as used in systems programming and give a practical example to illustrate how it can be used to handle errors in a block of codeb Using the Windows API write a CC system program to search for files in the Windows file system. Network topology is the topological structure of a.
For Network Engineers the ability to mirror switch traffic and send it to a sniffer for analysis is an essential troubleshooting technique. Sudo apt-get install wireshark. Wireshark automatically builds a graphical summary of the TCP flow.
On some Linux systems modemmanger blocks the port for about 20s after plug-in if this disturbs. W209 relay diagram relay 20 21 circuit diagram 3 6 DMM 16-18 duty cycle. Wireshark is the de facto tool for capturing and analysing network traffic.
Each row represents a single TCP packet. You have to select this corresponding port in the software. This layer is also known as Internet layer.
Unscientifically the Wireshark. How to capture packets. AMF Access and Mobility Function Sequence Diagram SMF Session Management Function.
5G Service-Based Architecture SBA. If you have any feedback please go to the Site Feedback and FAQ page. Wireshark indicates that network congestion has occurred and multiple acknowledgments cause the re-transmission of the problematic traffic by color-coding it.
Edit capture files D8. Information about each release can be found in the release notes. TCPIP network ports information for Hyper-V management and configuration dos and donts to connect your network and manage firewalls as necessary.
Search for wireshark and download the binary. Regarding adjusting the MTU to the right value Yes wireshark needs to be placed between the modem and the router to check what is the. Write the source codes c Discuss the files systems.
The initial Statusbar 322. Wireshark Users Guide. For a complete list of system requirements and supported platforms please consult the Users Guide.
While analysing packet captures in Wireshark it is even possible to extract files from the pcap that. All present and past releases can be found in our download area. The following diagram gives a generalized idea of where youll be working.
Therefore the entire suite is commonly referred to as TCPIPTCP provides reliable ordered and error-checked delivery of a stream of octets bytes between applications running. N102 is a device on the CAN-B in the overall network. Merging multiple capture files into one D9.
Network Repository Function. To improve network speed pinpointing the exact site of packet loss is critical. IBM Developer More than 100 open source projects a library of knowledge resources and developer advocates ready to help.
The Statusbar with a loaded capture file 323. Dump and analyze network traffic. All Cisco Catalyst switches support the Switched Port Analyzer SPAN feature which copies traffic from specified switch source ports or VLANs and mirrors this traffic to a specified destination switch.
Disable or remove the modemmanager. Cookie0x0 duration715529s table20 n_packets5 n_bytes830 hard_timeout. The main protocol used at this layer is IP.
Google docs tree diagram. Similar software includes tcpdump on Linux. By movement of data we generally mean routing of data over the network.
It lets you capture and interactively browse the traffic running on a computer network. However in the default configuration with multi-host the compute host is the gateway. 2011 Ford Edge Fuse Diagram for Battery Junction Box.
While ICMPused by popular ping command and IGMP are also used at this. Network topology can be used to define or describe the arrangement of various types of telecommunication networks including command and control radio networks industrial fieldbusses and computer networks. Location of Firewall Rules.
Network topology is the arrangement of the elements links nodes etc of a communication network. A network issue may cause problems at any point in the cloud. First step acquire Wireshark for your operating system.
The diagram depicts an external gateway. Network diagram is attached If I try to RDP to a 2008 server on the 300 network from ANY XP VISTA 7 client on the 200 network my rdp session. Each Windows package comes with the latest stable release of Npcap which is required for live.
Oct 20 2018 6 min read. F1 - Not used F2 - Not used F3 - Not used F4 30 Wiper Relay F5 40 Anti-lock Brake System ABS module F6 - Not used F7 30 LiftgateTrunk Module LTM F8 20 Roof opening panel motor assembly F9 20 Power point console rear F16 - Not used F17 - Not used F18 40 Blower motor relay. A packet is the smallest unit of information flowing in a network or between networks and theres a well-defined method of constructing and verifying network packets beyond the scope of this article but if youre feeling adventurous heres more.
A high number of duplicate acknowledgments indicates packet loss and significant delay in a network. The Transmission Control Protocol TCP is one of the main protocols of the Internet protocol suiteIt originated in the initial network implementation in which it complemented the Internet Protocol IP. The packet is now most likely out of your control at this point.
The main purpose of this layer is to organize or handle the movement of data on network. The Packet Diagram pane 321. To better understand how sequence and acknowledgement numbers are used throughout the duration of a TCP session we can utilize Wiresharks built-in flow graphing ability.
Every firewall configuration is a bit different. Packet flow in a network source. Windows or Mac OSX.

Wireshark Architecture Download Scientific Diagram

Capturing The Packets Using Wireshark Network Monitor Download Scientific Diagram
Do Network Traffic Analysis Using Wireshark And Other Tools By Antonyshinuaa Fiverr

Wireshark Evidence Output When Traffic Was Normal The Network To Force Download Scientific Diagram

The Results From The Wireshark Packets Capture Download Scientific Diagram

The Network Environment Consists Of Snort Wireshark Our Proposed Download Scientific Diagram

Component A And Data Flow Diagrams B For Wireshark Download Scientific Diagram

Wireshark Display Showing The Effect On The Network Of A Single Ping Download Scientific Diagram

Network Packets Captured By Wireshark Download Scientific Diagram

5 Example Wireshark Interface With A Live Packet Capture Download Scientific Diagram

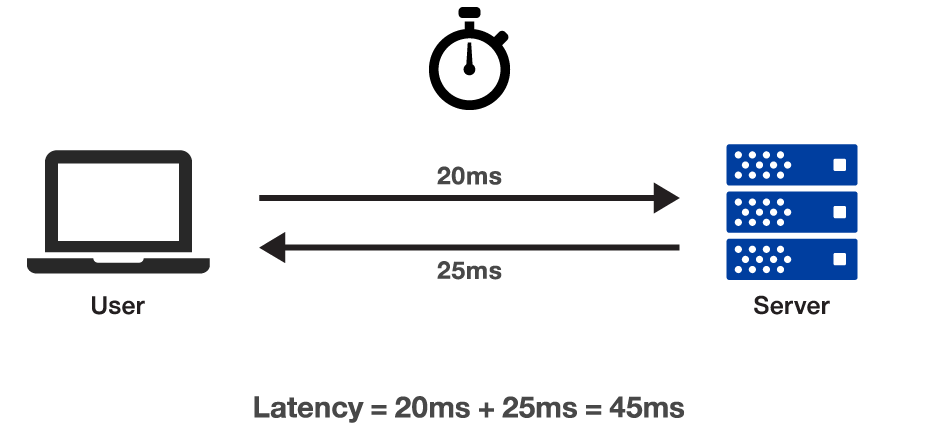
Troubleshooting Network Latency With Wireshark Geekflare
Network Packet Analysis Using Wireshark Download Scientific Diagram
Investigation Of Suspect Network Traffic With Wireshark Program Figure Download Scientific Diagram

Wireshark Architecture Download Scientific Diagram

Packets Captured Using Wireshark In Experiment 1 Download Scientific Diagram

Wireshark Architecture Download Scientific Diagram

Setup To Capture The Network Activity From The Mobile App Using Download Scientific Diagram